Respiratory physician Lutz Beckert considers chronic obstructive pulmonary disease management, including the prevention of COPD, the importance of smoking cessation and pulmonary rehabilitation, and the lifesaving potential of addressing treatable traits. He also discusses the logic of inhaler therapy, moving from single therapy to dual and triple therapy when indicated, as well as other aspects of management
How secure is your practice from cyberattack?
How secure is your practice from cyberattack?

Wellington GP and health IT columnist Richard Medlicott looks at what practices can do to avoid security breaches
“We can patch the systems, but we can't patch humans”
I always intended to write my third column on cybersecurity. The timing was coincidental with the recent incident at Pinnacle Midlands Health Network. At the time of writing, the extent of that particular breach is a bit unclear, but it does look fairly typical in the sense that it's a large healthcare organisation which has had its defences breached. And there’s resulting anxiety for both patients and the network as to what data might have been copied or accessed and what may come next.
Fortunately, we're not seeing a ransomware situation which must be incredibly difficult if you get caught up in that situation.
Hacking is a business, and like most businesses there's a profit motive, systems and continuous quality improvement to how the scams work.
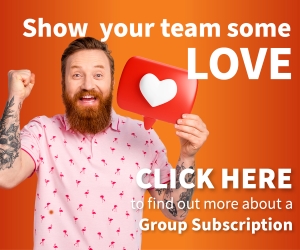
The diagram below shows the number of complaints made to the FBI Internet crime complaint center and published in the Federal Bureau of Investigation Internet Crime Report 2021. Most of those are static apart from phishing-type attacks.
Fortunately, we are not powerless to reduce our risk; we can never eliminate it, but we have a responsibility to protect our businesses and our patients’ information. Some aspects of this protection are complicated, and others are complex. By that I mean there are technical steps that you can take with your IT provider to ensure technical safety. That's the complicated part.
The current RNZCGP standards refer to a shortened version of the Health Information Security Framework that practices need to adhere to. That framework was 87 pages long and published about 10 years ago. It was intended for larger organisations such as DHBs. Patients First developed the abbreviated version which the college adopted for its standards. This security framework is being rewritten, and while I have not seen it, I do expect there will be greater requirements placed on general practice around data security.
There are a few things you can do. Firstly, I recommend having an external company that specialises in IT security do penetration testing on your systems. Tū Ora Compass PHO is subsidising this for practices in its region, and I hope to see other practices with us.
My practice was the first to do this within our PHO. We got a very detailed report back which we were able to share with our IT provider. It resulted in unexpected vulnerabilities that we then went on to patch. We were very satisfied that in the end we had done some significant work to improve our security position.
The test covered many aspects, such as our PMS, third-party software, Microsoft 365 settings, Wi-Fi passwords and security settings on third-party infrastructure, such as the telephone system and printers. I know we are not bulletproof, the only way to be truly secure from cybersecurity threats would be to go back to pen and paper and we can't do that! I feel, however, we are at least wearing a bulletproof vest which will lower our risk.
I expect that penetration testing will be a requirement for practices, and I know there will be many of you who feel this is another compliance cost put on us. But while there is some cost it is worthwhile insurance. The costs of a significant breach or ransomware are extremely high. You may wish to explore having cybersecurity insurance to help cover those costs if you do get breached.
The other area is a little bit more complex than complicated. We can patch the systems, but we can't patch humans. Many of the successful attacks on businesses come through the vulnerabilities that you or your staff may present. It's important to have policies in place that cover staff onboarding and exit, staff awareness training of phishing attacks, how you manage your contractors coming in and out of the building and how you manage your security when working from home.
In terms of training, we worked with our IT providers to put in place an online training package that simulates phishing attacks. We have a button in Outlook that staff can press when they think they've received a phishing email. If they do hit “open” on a simulated phishing email and they are directed to further training.
The staff have been fine with this, it has raised awareness of phishing attacks and how to spot suspicious emails. The system comes with monitoring and outcome measurement such as the diagram below.
We use multi-factor authentication for accessing our system when working from home. This means we need a username, a password and a device. If working from home without using multifactor authentication you should talk with your IT provider about getting it set up.
Below are some useful organisations to contact for a response to a cybersecurity attack:
-
certnz - www.cert.govt.nz
-
The National Cyber Security Centre (NCSC) - www.ncsc.govt.nz
-
netsafe - www.netsafe.org.nz
Our penetration testing was provided by Managed Security Service Provider for Healthcare Organisations - Medical IT Advisors (meditadvisors.com)
Our Phishing training and management is supplied by www.knowbe4.com.
We're publishing this article as a FREE READ so it is Free to read and Easy to share more widely. Please support us and our journalism – subscribe here








![Barbara Fountain, editor of New Zealand Doctor Rata Aotearoa, and Paul Hutchison, GP and senior medical clinician at Tāmaki Health [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/Barbara%20Fountain%2C%20editor%20of%20New%20Zealand%20Doctor%20Rata%20Aotearoa%2C%20and%20Paul%20Hutchison%2C%20GP%20and%20senior%20medical%20clinician%20at%20T%C4%81maki%20Health%20CR%20Simon%20Maude.jpg?itok=-HbQ1EYA)
![Lori Peters, NP and advanced health improvement practitioner at Mahitahi Hauora, and Jasper Nacilla, NP at The Terrace Medical Centre in Wellington [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/2.%20Lori%20Peters%2C%20NP%20and%20advanced%20HIP%20at%20Mahitahi%20Hauora%2C%20and%20Jasper%20Nacilla%2C%20NP%20at%20The%20Terrace%20Medical%20Centre%20in%20Wellington%20CR%20Simon%20Maude.jpg?itok=sUfbsSF1)
![Ministry of Social Development health and disability coordinator Liz Williams, regional health advisors Mary Mojel and Larah Takarangi, and health and disability coordinators Rebecca Staunton and Myint Than Htut [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/3.%20Ministry%20of%20Social%20Development%27s%20Liz%20Williams%2C%20Mary%20Mojel%2C%20Larah%20Takarangi%2C%20Rebecca%20Staunton%20and%20Myint%20Than%20Htut%20CR%20Simon%20Maude.jpg?itok=9ceOujzC)
![Locum GP Helen Fisher, with Te Kuiti Medical Centre NP Bridget Woodney [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/4.%20Locum%20GP%20Helen%20Fisher%2C%20with%20Te%20Kuiti%20Medical%20Centre%20NP%20Bridget%20Woodney%20CR%20Simon%20Maude.jpg?itok=TJeODetm)
![Ruby Faulkner, GPEP2, with David Small, GPEP3 from The Doctors Greenmeadows in Napier [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/5.%20Ruby%20Faulkner%2C%20GPEP2%2C%20with%20David%20Small%2C%20GPEP3%20from%20The%20Doctors%20Greenmeadows%20in%20Napier%20CR%20Simon%20Maude.jpg?itok=B0u4wsIs)
![Rochelle Langton and Libby Thomas, marketing advisors at the Medical Protection Society [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/6.%20Rochelle%20Langton%20and%20Libby%20Thomas%2C%20marketing%20advisors%20at%20the%20Medical%20Protection%20Society%20CR%20Simon%20Maude.jpg?itok=r52_Cf74)
![Specialist GP Lucy Gibberd, medical advisor at MPS, and Zara Bolam, urgent-care specialist at The Nest Health Centre in Inglewood [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/7.%20Specialist%20GP%20Lucy%20Gibberd%2C%20medical%20advisor%20at%20MPS%2C%20and%20Zara%20Bolam%2C%20urgent-care%20specialist%20at%20The%20Nest%20Health%20Centre%20in%20Inglewood%20CR%20Simon%20Maude.jpg?itok=z8eVoBU3)
![Olivia Blackmore and Trudee Sharp, NPs at Gore Health Centre, and Gaylene Hastie, NP at Queenstown Medical Centre [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/8.%20Olivia%20Blackmore%20and%20Trudee%20Sharp%2C%20NPs%20at%20Gore%20Health%20Centre%2C%20and%20Gaylene%20Hastie%2C%20NP%20at%20Queenstown%20Medical%20Centre%20CR%20Simon%20Maude.jpg?itok=Z6u9d0XH)
![Mary Toloa, specialist GP at Porirua and Union Community Health Service in Wellington, Mara Coler, clinical pharmacist at Tū Ora Compass Health, and Bhavna Mistry, specialist GP at Porirua and Union Community Health Service [Image: Simon Maude]](/sites/default/files/styles/thumbnail_cropped_100/public/2025-03/9.%20Mary%20Toloa%2C%20Porirua%20and%20Union%20Community%20Health%20Service%20in%20Wellington%2C%20Mara%20Coler%2C%20T%C5%AB%20Ora%20Compass%20Health%2C%20and%20Bhavna%20Mistry%2C%20PUCHS%20CR%20Simon%20Maude.jpg?itok=kpChr0cc)